Creating a Comprehensive Cyber Incident Response Plan for Your Small Business

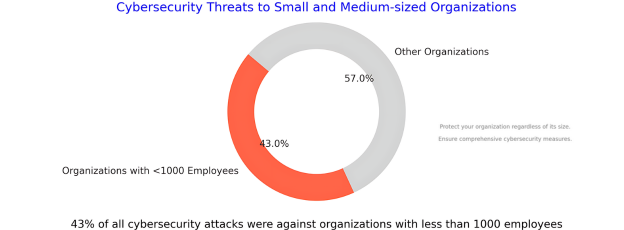
Small businesses are increasingly targeted by cybercriminals. Many small business owners think their business is too small to attract such attention, but this belief could not be further from the truth and will leave a business vulnerable to attack. A recent Verizon incident response team study revealed that 46% of all database breaches impacted businesses with fewer than 1000 employees. Furthermore, 82% of all ransomware attacks were against companies with less than 1000 employees. To mitigate these risks, it is crucial to have a comprehensive Cyber Incident Response Plan (CIRP). This guide will help you understand how to create an effective CIRP tailored to your business needs.
Understanding the Importance of a Cyber Incident Response Plan
A CIRP outlines the procedures your business will follow during a cybersecurity incident. Its primary goals are to:
- Minimize damage and reduce recovery time and costs.
- Protect sensitive data and maintain customer trust.
- Comply with legal and regulatory requirements.
- Ensure business continuity.
Assemble a Response Team
The first step in creating your CIRP is assembling a response team. This team should include:
- Team Leader: Responsible for overall coordination and decision-making.
- IT Specialist: Manages technical aspects, such as system recovery and securing networks.
- Communications Officer: Handles internal and external communications, including notifying affected parties and media.
- Legal Advisor: Ensures compliance with legal and regulatory requirements.
- HR Representative: Addresses employee-related issues and concerns.
Identify and Prioritize Assets
Identify all critical assets that need protection, including:
- Data: Customer data, financial records, intellectual property.
- Systems: Servers, databases, applications.
- Infrastructure: Network equipment, security devices.
- Personnel: Key employees and their roles in the response.
Prioritize these assets based on their importance to your business operations and the potential impact of their compromise.
Develop Response Procedures
Please ensure that your CIRP contains detailed procedures for handling various types of cyber incidents. Some common scenarios to consider are:
- Data Breaches: Steps for containing the breach, securing affected systems, and notifying impacted individuals.
- Ransomware Attacks: Procedures for isolating infected systems, evaluating the feasibility of data recovery without paying ransom, and restoring operations from backups.
- Phishing Attacks: Measures for identifying and mitigating the impact of successful email phishing attempts, as well as enhancing employee awareness and training.
- Be sure to outline specific actions for team members for each scenario, covering technical steps, communication protocols, and documentation requirements.
Establish Communication Protocols
Effective communication is crucial during a cyber incident. It’s important to establish clear protocols for:
- Internal Communication: Determine how and when to inform employees, management, and the board of directors.
- External Communication: Notify customers, partners, regulatory bodies, and the media. Make sure that communications are clear, concise, and comply with legal requirements.
- Incident Reporting: Set up a system for employees to report suspicious activities or potential incidents promptly.
Implement Detection and Monitoring Systems
Early detection of cyber incidents can significantly reduce their impact. Implement systems and tools to monitor your network and detect unusual activities. Regularly update and test these systems to ensure their effectiveness.
Conduct Regular Training and Drills
Make sure all employees understand their roles and responsibilities in the CIRP. Conduct regular training sessions and simulated drills to:
- Test the effectiveness of the response plan.
- Identify areas for improvement.
- Ensure that team members are familiar with the procedures and can act quickly during an incident.
Review and Update the Plan Regularly
Cyber threats are always changing, so your CIRP should, too. Review and update your plan at least once a year or after any major changes to your business or IT setup. Use what you’ve learned from practice drills and real incidents to improve the plan constantly.
Document and Learn from Incidents
After experiencing a cyber incident, it’s important to thoroughly analyze what occurred, how it was managed, and how to enhance the
response plan to prevent future similar incidents.
Conclusion
A small business must have a comprehensive Cyber Incident Response Plan to safeguard against a cyber incident’s disastrous impacts. By forming a proficient response team, pinpointing critical assets, creating detailed response procedures, and consistently reviewing and enhancing the plan, you can ensure that your business is ready to counter cyber threats effectively. These measures will shield your business and uphold the trust of your customers and stakeholders.
Share:
Disclosures
The material on this site was created for educational purposes. It is not intended to be and should not be treated as legal, tax, investment, accounting, or other professional advice.
Securities and Insurance Products:
NOT A DEPOSIT | NOT FDIC INSURED | NOT BANK GUARANTEED | NOT INSURED BY ANY FEDERAL GOVERNMENT AGENCY | MAY LOSE VALUE
