Previous Blog Posts
Continue to our Previous Blog Posts

You've probably gotten pretty good at spotting phishing emails. That suspicious link? You're not clicking it. That urgent message from your "bank"? You're checking the sender's address first. You're doing exactly what security experts have been teaching for years.
Unfortunately, cybercriminals know you've gotten smarter. They've noticed that email filters are catching more malicious links, and users are finally questioning those "click here immediately" buttons. So, they've adapted with a surprisingly low-tech twist on an old scam by getting you to call them instead.

TOAD stands for Telephone Oriented Attack Delivery, though you might also hear it called Call-Back Fraud. It's a social engineering attack that weaponizes something we still largely trust: our telephone and the voice on the other end. Instead of trying to sneak a malicious link past increasingly sophisticated email security systems, attackers send emails designed to make you pick up the phone and dial a number.
The brilliance of this approach is that it sidesteps all those technical defenses we've built up. Your email security can't scan a phone conversation. Your antivirus software can't detect a fraudulent voice on the other end of a call. And many people still inherently trust phone interactions more than digital ones.
The attack typically begins with an email that creates urgency or concern. Common scenarios include fake invoices for expensive purchases you didn't make, subscription renewals for services you don't use, or security alerts about your account. The key element? A prominent phone number encouraging you to "call immediately to cancel" or "contact customer service to resolve this issue."
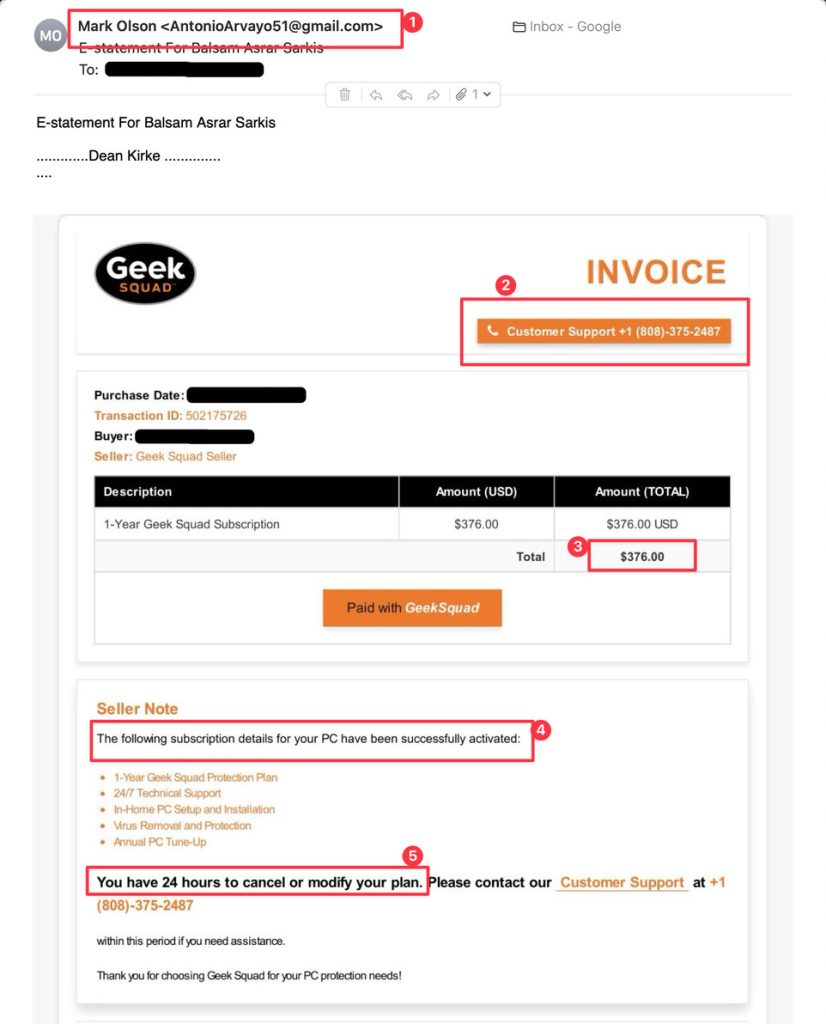
When you call that number, you're connected to a fraudster posing as a legitimate customer service representative. They're prepared, professional, and convincing. During the call, they may ask you to:
The attacker uses the phone conversation to build trust and exploit the natural human tendency to want to resolve problems quickly. They create pressure, use technical jargon, and leverage your desire to fix what seems like a legitimate issue. Stay safe with these preventive measures:
Verify independently. If you receive an unexpected email about charges, subscriptions, or account issues, don't use the contact information provided. Instead, look up the company's official website yourself and use the contact details listed there.
Question urgency. Legitimate companies rarely demand immediate action. Pressure tactics are a red flag.
Never provide sensitive information. Real customer service representatives won't ask for passwords, full credit card numbers, or remote access to your computer through unsolicited contact.
When in doubt, hang up. There's no penalty for ending a call if something feels wrong. You can always initiate contact through official channels if needed.
The technology protecting us is impressive but remember: the most effective security tool is still your good judgement. Stay skeptical, verify independently, and don't let fear and urgency override your common sense.
December 24, 2025
Many of you may find a new Apple iPhone under the tree this year. However, Apple devices often come with default settings that prioritize convenience …
September 1, 2025
Your phone rings, displaying your bank’s name on the caller ID. The caller’s voice is professional and urgent, stating “We’ve observed suspicious activity on your …
August 12, 2025
Nothing is out of bounds for scammers, and now they’re targeting churches and the people in them. One way they do this is by using …
June 10, 2025
A bank customer recently shared that their identity theft monitoring service alerted them that their Social Security number had been discovered online, linked to an …
April 15, 2025
The appeal of remote work has grown significantly, providing flexibility and convenience for many individuals. However, this shift has unfortunately resulted in a troubling rise …
March 14, 2025
You’ve probably heard of hacked emails or social media accounts, but now, scammers target financial accounts, leading to potential economic losses and stolen personal information. …
February 28, 2025
Small business owners often ask, “What’s the one low or no-cost action I can take that will immediately improve the security of my business?” The …
January 21, 2025
Tax season is stressful enough without worrying about fraud. Unfortunately, cybercriminals and scammers exploit this time of year to deceive unsuspecting individuals and businesses into …
January 3, 2025
In neighborhoods across the country, a troubling trend is rising: thieves targeting residential mailboxes in search of valuable items, particularly personal checks. What might seem …
December 17, 2024
The holiday season often brings new electronics as gifts, including mobile phones. While upgrading to the latest device is exciting, many people overlook a crucial …
November 14, 2024
The holiday season is upon us, and for many, that means the excitement of finding the perfect gifts online! A recent report from Drive Research …
October 24, 2024
Some great football games are being played across the Mid Penn Bank footprint, with many of our resident teams having stellar seasons. The most popular …


The Mid Penn Bank Cybersecurity team studies the ever-changing cyber threats and the actions necessary to mitigate those threats. We look to be a guide to our customers throughout their cybersecurity research. Please contact us with your questions!
Please be aware you are leaving Mid Penn Bank's web site. You are being redirected to a linked site (hereafter referred to as 'site') for your convenience. The content appearing on this site is third-party content. Mid Penn Bank is not responsible for providing or updating the information found on this site. This site is provided as an informational source only.
ProceedWe advise you not to email confidential information such as account number(s) or your social security number.
Proceed